The Client-Server Connection: Unlocking Distributed Systems
Understand the principles behind this powerful architecture and its role in modern computing
In today's digital world, we're constantly interacting with technology, often without fully grasping how it all works behind the scenes. From checking your email to streaming your favorite shows, much of what we do online relies on a fundamental structure called client-server architecture.
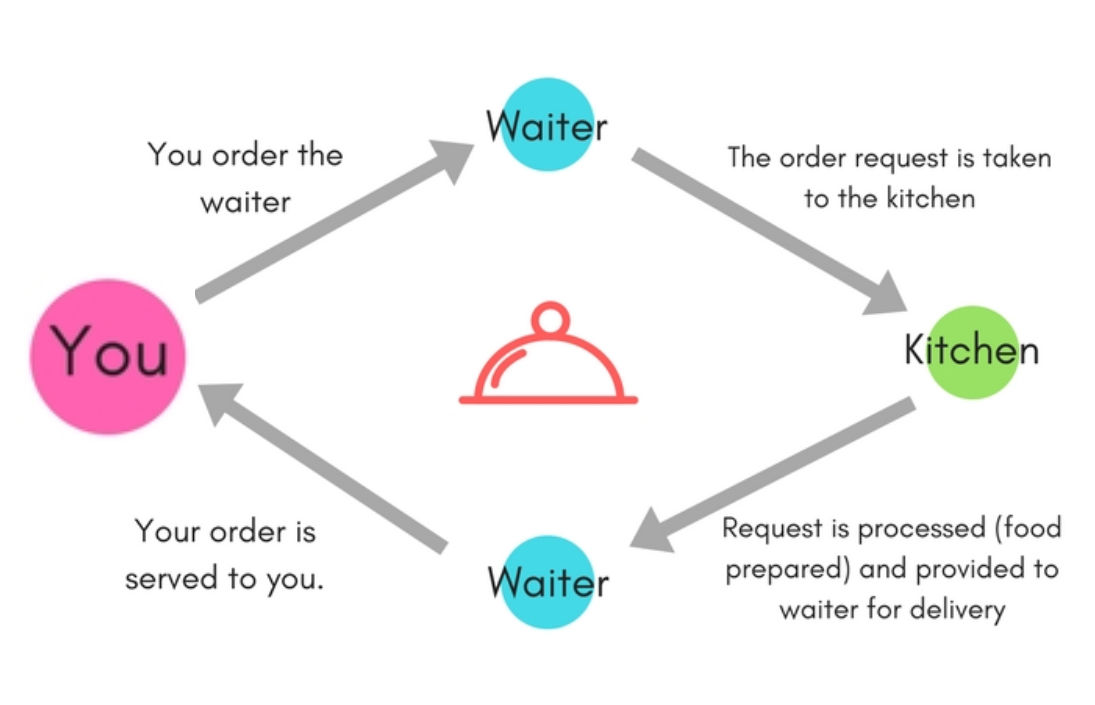
Think of it as a restaurant. You, the customer, are the client. You place an order (a request) with the waiter. The waiter relays your order to the kitchen (the server), which prepares your food and sends it back to you through the waiter.
In this analogy, your computer or phone is the client, and the remote computer providing data is the server.
Still confused? Let’s dive into it for a better understanding.
What is Client-Server Architecture?
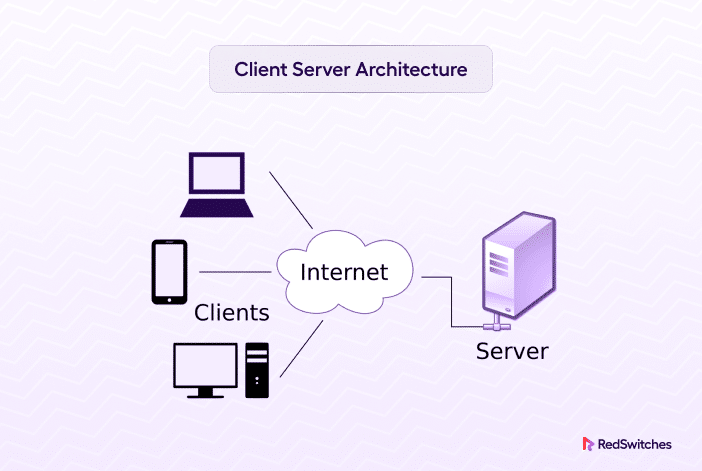
At its core, client-server architecture is a distributed computing model where tasks are divided between clients (devices requesting services) and servers (computers providing those services).
Clients initiate requests, and servers process those requests and deliver the necessary resources or data.
Let us look at the main components of this architecture:
- CLIENT: A device or software application that makes a request for a service or resource. Examples include online browsers, email clients, and mobile applications.
- SERVER: A computer or software system that delivers services or resources to clients. Servers can be categorized as web servers, file servers, or database servers.
- NETWORK: The communication route that enables clients and servers to interact. This could be the internet, a LAN, or a WAN.
- PROTOCOL: A set of rules that regulate client-server communication. HTTP is a common protocol for online browsing, SMTP for email, and FTP for file transfer.
The Client-Server Model at Work
To understand how client-server architecture works, consider a simple example: web browsing.
Here's a step-by-step breakdown:
1) User Request: You enter a website's URL into your browser (the client).
2) DNS Lookup: Your browser sends a request to a Domain Name System (DNS) server to find the website's IP address.
3) Server Request: Once the IP address is obtained, your browser sends an HTTP request to the web server's IP.
4) Server Response: The web server processes your request and sends back the necessary files.
5) Rendering: Your browser renders these files to display the website.
And you wouldn’t ever guess, but …
… THE CLIENT-SERVER MODEL IS EVERYWHERE
- WEB BROWSING: When you type a website address into your browser (the client), your browser sends a request to the web server hosting the website. The server then sends back the website's code, which your browser renders to display the page.
- EMAIL: Your email client (e.g., Gmail, Outlook) is the client. When you send an email, your client sends the message to an email server, which then routes it to the recipient's email server. When you receive an email, your client retrieves it from your email server.
-ONLINE GAMING: In online games, your gaming device is the client, and the game server hosts the game world and manages interactions between players.
- CLOUD STORAGE: When you store files on a cloud service like Google Drive or Dropbox, your computer or phone is the client, and the cloud provider's servers store your files.
The Benefits and Downfalls of Such Architecture
This architecture provides numerous benefits due to its groundbreaking features, including:
CENTRALIZED RESOURCES: Servers can grant access to shared resources like databases, files, and applications, making them easier to administer and maintain.
SCALABILITY: Client-server systems can be easily scaled to meet growing demand by adding or upgrading existing servers.
SECURITY: Servers can use security measures to keep data and resources safe from unauthorized access.
MANAGEABILITY: Centralized server management streamlines chores like software upgrades, backups, and security patching.
YET is not free of flaws, and has several potential drawbacks that can lead to its downfall in certain scenarios:
SINGLE POINT OF FAILURE:
The central server acts as a single point of failure. If the server fails or is compromised, the entire system can become unavailable, impacting all connected clients. This is the case as servers are often the target of cyber attacks.
NETWORK DEPENDENCY:
The architecture heavily relies on network connectivity. Network congestion or outages can significantly affect system performance and availability.
HIGH SETUP COSTS AND RESOURCES UTILIZATION:
Setting up and maintaining servers can be expensive due to the need for robust hardware and skilled personnel while on the other hand they require a significant amount of resources to handle client traffic efficiently = increased operational costs $$$
COMPLEXITY & MAINTENANCE:
Implementing and maintaining a client-server architecture can be complex, requiring expertise in networking, security, and server administration. Also compatibility can present issues.
LIMITED AUTONOMY AND PRIVACY:
Clients must communicate with a central server, which can reduce privacy and autonomy compared to decentralized architectures like peer-to-peer networks.
Building on the themes we explore here, it's crucial to consider the security implications inherent in client-server models, as discussed in my previous articles. [Link below]
As previously stated, vulnerabilities in either the client or the server can provide entry points for hostile actors. A compromised web server, for example, can spread malware to unwitting users. Securing both sides of this digital bond is critical. Understanding how data flows across these architectures is the first step toward preserving your digital footprint. Knowing how your data is requested, processed, and stored allows you to make more educated choices regarding your privacy and security.
Do you use end-to-end encryption? Are you aware of the server's location and data security policies?
These are essential questions in today's digital environment.
Conclusion
Many of the technologies we use on a daily basis are built on a client-server design. Understanding how it works allows us to appreciate the complexities of the digital world and make better decisions about our online activity. As technology advances, it is critical to understand the underlying structures that influence our digital experiences, particularly in terms of security and privacy.